
With Akord, you own the keys that encrypt and decrypt your data. Your keys are generated when you sign up and are represented by your backup phrase. In this article article, we'll explain the backup phrase, how we store and manage it, and demonstrate exactly how you 'own the keys'.
使用 Akord,您才拥有加密和解密数据的密钥。您的密钥是在您注册时生成的,并由您的备份短语表示。在本文中,我们将解释备份短语、我们如何存储和管理它,并精确演示您如何“拥有密钥”。
关于您的备份短语 (Your backup phrase explained)
For many web3 services, the backup phrase is required any time you would like to access your wallet from a new device. Let's first explain what the backup phrase is.
对于许多 web3 服务,只要您想从新设备访问您的钱包,就需要备份短语。我们先来解释一下什么是备份短语。
In order to generate unique keys, we need a unique random number that is known as a “seed”. Since it is difficult for us to read a large number, crypto-wallets use a backup phrase, which is a human-readable representation of the seed. It is also known by other names such as seed phrase, recovery phrase, mnemonic, or passphrase.
为了生成唯一的密钥,我们需要一个被称为“种子”的唯一随机数。由于人类很难读取大量数字,因此加密钱包使用备用短语,其实是种子的人类可读表示。它也有其他名称,例如种子短语、恢复短语、助记词或密码短语。
The backup phrase is typically generated using an algorithm called BIP39 and assigned to a user when signing up. Akord uses this method to generate the backup phrase. It consists of 12 or 24 words that are chosen from a list of 2,048 words beginning with “abandon” and ending with “zoo”.
备用短语通常使用称为 BIP39 的算法生成,并在注册时分配给用户。 Akord 使用这种方法来生成备份短语。它由从 2,048 个单词 列表中选择的 12 或 24 个单词组成,以“abandon”开头并结束与“zoo”。
How safe is a backup phrase that is made up of 12 words? Well, since there are plenty of possible combinations, the chance of drawing the right combination is 1 out of the big number below:
由 12 个单词组成的备用短语有多安全?好吧,因为有很多可能的组合,所以得出正确组合的机会是下面大数字中的 1:
2,048^12 = 5444517870735015415413993718908291383296 ≈ 5.4445179e+39
So, as you can see, backup phrase is pretty much impossible to hack from a brute force attack that tries to guess what your backup phrase is. You just need to store it in a safe place.
因此,正如您所看到的,备用短语几乎不可能从试图猜测您的备用短语是什么的蛮力攻击中破解。您只需将其存放在安全的地方。
We recommend the following security practices:
我们推荐以下安全做法:
- Store your backup phrase in a few different secure locations offline.
将您的备份短语离线存储在几个不同的安全位置。 - Don’t communicate your backup phrase to anyone.
不要将您的备用短语传达给任何人。 - Don’t store your backup phrase unencrypted digitally.
不要以数字方式存储未加密的备份短语。
您拥有 Akord 上的备用短语 (You own the backup phrase on Akord)
In Akord, we ask for an email address and password. We ask for your email so we can send you important notifications when other people in your vault take actions. Your password is used to decrypt your backup phrase locally when you want to sign in.
在 Akord,我们要求提供电子邮件地址和密码。我们要求您提供电子邮件,以便在您保管库中的其他人采取行动时向您发送重要通知。当您要登录时,您的密码用于在本地解密您的备份短语。
The backup phrase is encrypted using your actual password. This means that nobody can decrypt your backup phrase without knowing your password.
备份短语使用您的实际密码加密。这意味着没有人可以在不知道您的密码的情况下解密您的备份短语。
We store the following three things in our database:
我们在数据库中存储以下三项内容:
1.E-mail address(电子邮件地址)
2.Encrypted backup phrase(加密备份短语)
3.Verifier of the password(密码验证者)
We do not store your password, but rather a cryptographic verifier of it. This means that we can easily check if a password you entered is correct without ever seeing the password itself. For those who are curious about how this works in detail, you can read about this process in the Secure Remote Password protocol (SRP).
我们不存储您的密码,而是对其进行加密验证。这意味着我们可以轻松检查您输入的密码是否正确,而无需查看密码本身。对于那些对其详细工作原理感到好奇的人,您可以在 安全远程密码协议 (SRP) 中阅读有关此过程的信息。
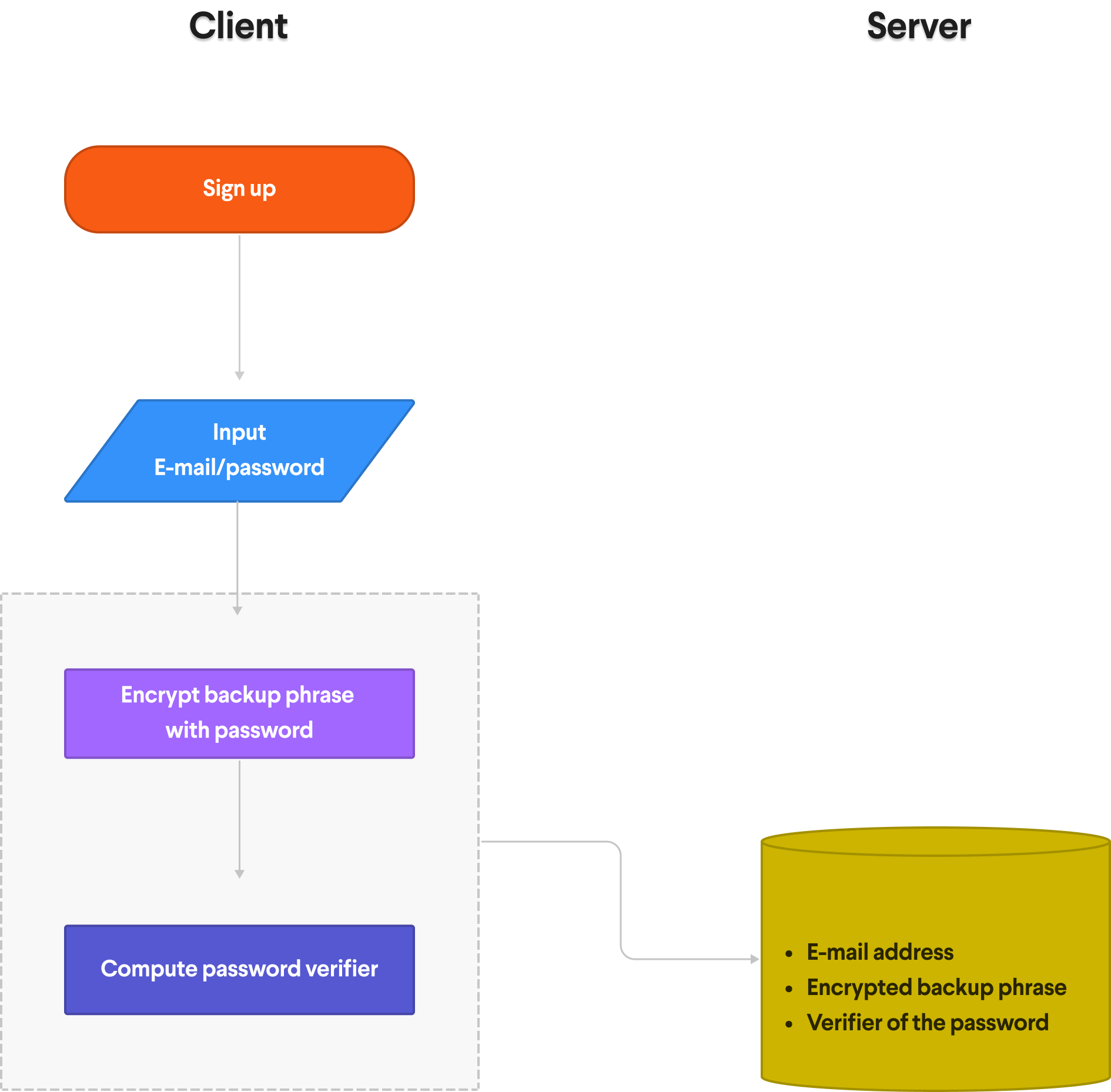
So here’s the process when you sign up with your email address and password. First, we encrypt your backup phrase with the password you entered, or more precisely, with a key derived from your password using PBKDF2. Then, we use the SRP protocol, to compute a cryptographic verifier: We send these two pieces of information along with your email address to our server. This makes it impossible for any middleman, or for anyone with access to the data, including Akord, to decrypt your backup phrase or obtain any information about your password.
以上是您使用电子邮件地址和密码注册的过程。首先,我们使用您输入的密码加密您的备份短语,或者更准确地说,使用 PBKDF2 使用从您的密码派生的密钥来加密。然后,我们使用 SRP 协议来计算加密验证器:我们将这两条信息连同您的电子邮件地址一起发送到我们的服务器。这使得任何中间人或任何有权访问数据的人(包括 Akord)都无法解密您的备份短语或获取有关您的密码的任何信息。
Akord 的简单登录 (Akord’s simple sign in)
Most web3 services require you to connect with a wallet, but with Akord you just need your email and password. So how exactly are you using your keys to sign in?
大多数 web3 服务都要求您连接钱包,但使用 Akord,您只需要您的电子邮件和密码。那么,您究竟是如何使用密钥登录的呢?
When you sign in, we first look up your email address and use the SRP protocol to make sure that the password you provided is correct, again, without actually sending the password. If the provided email and password are correct, we send back the encrypted backup phrase. It is decrypted directly in your browser, meaning that nobody but you ever knows it.
当您登录时,无需实际发送密码,我们首先会查找您的电子邮件地址并使用 SRP 协议,来确保您提供的密码正确无误。如果提供的电子邮件和密码正确,我们会发回加密的备份短语。它直接在您的浏览器中解密,这意味着除了您之外没有人知道它。
At this point, you're ready to use our user-friendly UI to upload your files to Arweave, with all encryption and decryption happening directly in your browser .
此时,您已准备好使用我们用户友好的 UI 将您的文件上传到 Arweave,所有加密和解密都直接在您的浏览器中进行。
We believe in true collaboration with the people using our product. If you have feedback on Akord, the best place to reach us is by becoming part of our community on Discord.
我们相信与使用我们产品的人的真正合作。如果您对 Akord 有任何反馈,与我们联系的最佳方式是加入 Discord 上的社区。

